Difference between revisions of "Post Exploitation"
Jump to navigation
Jump to search
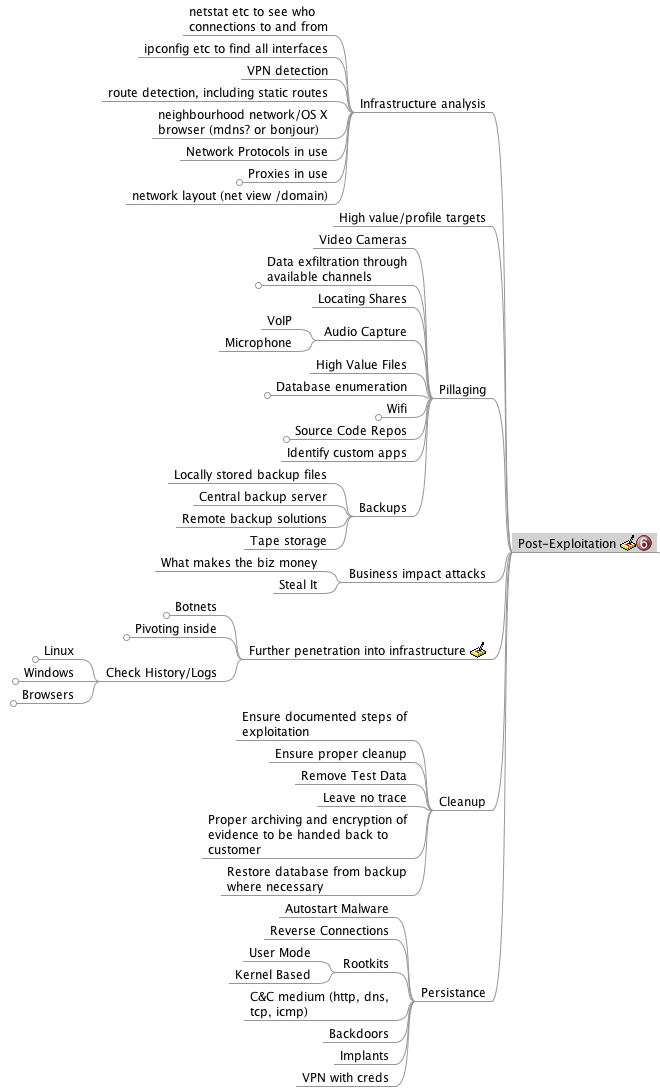
(Created page with "This section details the post-exploitation elements that should be addressed in a penetration test.<br /> Following is an image depicting the main branches of the corresponding m...") |
m (moved Post-exploit to Post Exploitation) |
(No difference)
| |